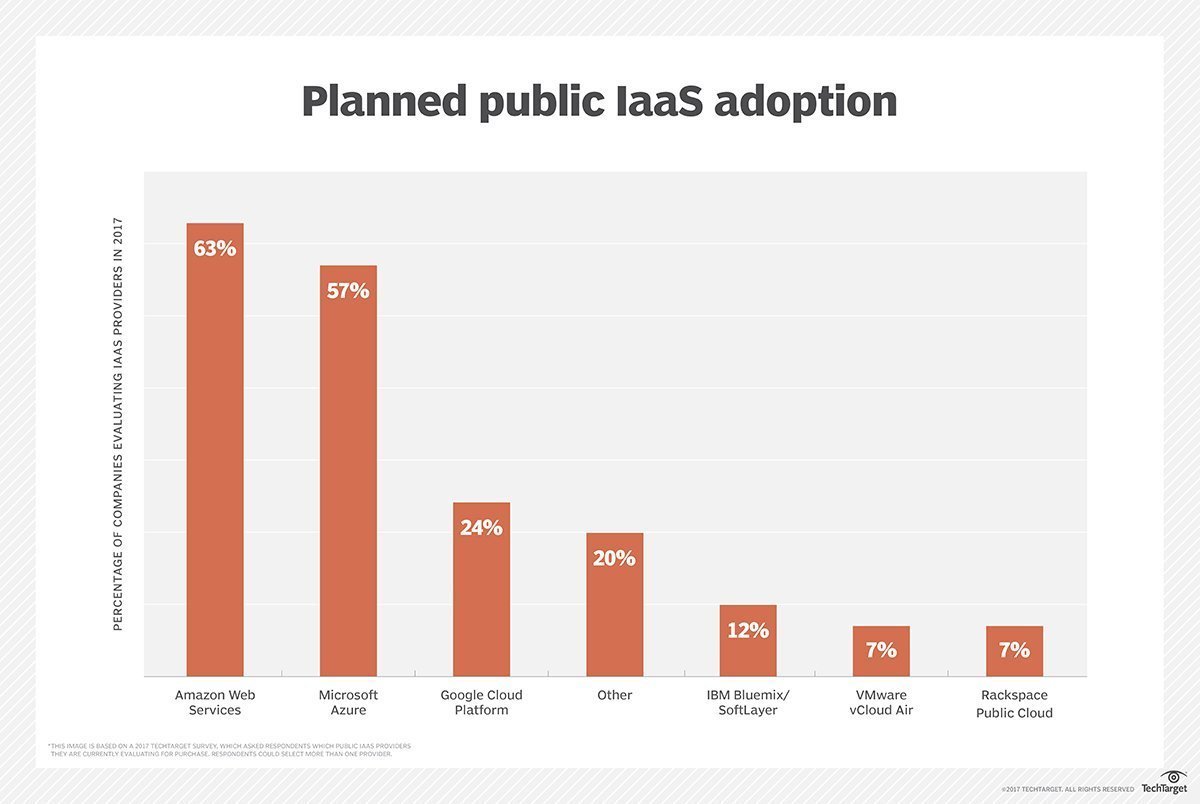
VIRTUAL PRIVATE NETWORKS
 One of the most important skills any computer user should have is the ability to use a virtual private network (VPN) to protect their privacy. A VPN is typically a paid service that keeps your web browsing secure and private over public Wi-Fi hotspots. VPNs can also get past regional restrictions for video- and music-streaming sites and help you evade government censorship restrictions—though that last one is especially tricky.
One of the most important skills any computer user should have is the ability to use a virtual private network (VPN) to protect their privacy. A VPN is typically a paid service that keeps your web browsing secure and private over public Wi-Fi hotspots. VPNs can also get past regional restrictions for video- and music-streaming sites and help you evade government censorship restrictions—though that last one is especially tricky.How it works
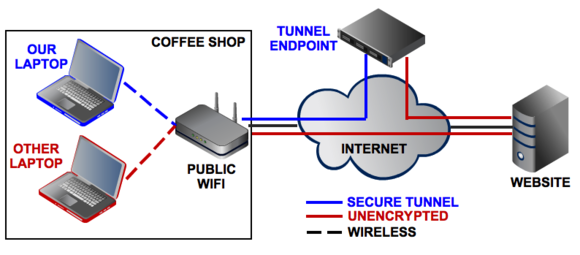
The best way to think of a VPN is as a secure tunnel between your PC and destinations you visit on the internet. Your PC connects to a VPN server, which can be located in the United States or a foreign country like the United Kingdom, France, Sweden, or Thailand. Your web traffic then passes back and forth through that server. The end result: As far as most websites are concerned, you’re browsing from that server’s geographical location, not your computer’s location.
We’ll get to the implications of a VPN’s location in a moment, but first, let’s get back to our secure tunnel example. Once you’re connected to the VPN and are “inside the tunnel,” it becomes very difficult for anyone else to spy on your web-browsing activity. The only people who will know what you’re up to are you, the VPN provider (usually an HTTPS connection can mitigate this), and the website you’re visiting.
When you’re on public Wi-Fi at an airport or café, that means hackers will have a harder time stealing your login credentials or redirecting your PC to a phony banking site. Your Internet service provider (ISP), or anyone else trying to spy on you, will also have a near impossible time figuring out which websites you’re visiting.
On top of all that, you get the benefits of spoofing your location. If you’re in Los Angeles, for example, and the VPN server is in the U.K., it will look to most websites that you’re browsing from there, not southern California.
This is why many regionally restricted websites and online services such as BBC’s iPlayer or Sling TV can be fooled by a VPN. I say “most” services because some, most notably Netflix, are fighting against VPN (ab)use to prevent people from getting access to, say, the American version of Netflix when they’re really in Australia.
For the most part, however, if you’re visiting Belgium and connect to a U.S. VPN server, you should get access to most American sites and services just as if you were sitting at a Starbucks in Chicago.
What a VPN can’t do
While VPNs are an important tool, they are far from foolproof. Let’s say you live in an oppressive country and want to evade censorship in order to access the unrestricted web. A VPN would have limited use. If you’re trying to evade government restrictions and access sites like Facebook and Twitter, a VPN might be useful. Even then, you’d have to be somewhat dependent on the government’s willingness to look the other way.
Anything more serious than that, such as mission-critical anonymity, is far more difficult to achieve—even with a VPN. Privacy against passive surveillance? No problem. Protection against an active and hostile government? Probably not.
The problem with anonymity is there are so many issues to consider—most of which are beyond the scope of this article. Has the government surreptitiously installed malware on your PC in order to monitor your activity, for example? Does the VPN you want to use have any issues with data leakage or weak encryption that could expose your web browsing? How much information does your VPN provider log about your activity, and would that information be accessible to the government? Are you using an anonymous identity online on a PC that you never use in conjunction with your actual identity?
Anonymity online is a very difficult goal to achieve. If, however, you are trying to remain private from prying eyes or evade NSA-style bulk data collection as a matter of principle, a reputable VPN will probably be good enough.
Beyond surveillance, a VPN also won’t do much to keep advertisers from tracking you online. Remember that the website you visit is aware of what you do on its site and that applies equally to advertisers serving ads on that site.
To prevent online tracking by advertisers and websites you’ll still need browser add-ons like Ghostery, Privacy Badger, and HTTPS Everywhere.
How to choose a VPN provider
There was a time when using a VPN required users to know about the built-in VPN client for Windows or universal open-source solutions such as OpenVPN. Nowadays, however, nearly every VPN provider has its own one-click client that gets you up and running in seconds. There are usually mobile apps as well to keep your Android or iOS device secure over public Wi-Fi.
The bad news for anyone used to free services is that it pays to pay when it comes to a VPN. There are tons of free options from reputable companies, but these are usually a poor substitute for the paid options. Free services usually allow a limited amount of bandwidth usage per month or offer a slower service. Tunnel Bear, for example, offers just 500MB of free bandwidth per month, while CyberGhost offers a free service that is significantly slower than its paid service.Of course that brings up another problem. Since there are so many services to choose from, how can you tell which ones are worth using? PCWorld has taken care of much of the legwork with its Best VPN services roundup. [Spoiler alert: It found Mullvad to be a great all-around VPN for its above-and-beyond commitment to user privacy, and NordVPN to be the current choice for watching U.S. Netflix from abroad.]
Then there are the free VPNs that use an ad-supported model, which in my experience usually aren’t worth using at all. Plus, free VPNs are usually anything but; in lieu of payment they may be harvesting your data (in anonymized form of course) and selling it as “marketing insights” to advertisers.
The good news is VPNs aren’t expensive. You can usually pay as little as $5 a month (billed annually or in blocks of several months) for VPN coverage.
What features to look for
Here are some issues to consider when shopping around for a VPN provider.
First, what kind of logging does your VPN provider do? In other words, what information do they keep about your VPN sessions and how long is it kept? Are they recording the IP addresses you use, the websites you visit, the amount of bandwidth used, or any other key details?
All VPNs have to do some kind of logging, but there are VPNs that collect as little data as possible and others that aren’t so minimalist. On top of that, some services discard their logs in a matter of hours or days while other companies hold onto them for months at a time. How much privacy you expect from your VPN-based browsing will greatly influence how long you can stand having your provider maintain your activity logs—and what those logs contain.
 TunnelBear
TunnelBear
Second, what are the acceptable terms of use for your VPN provider? Thanks to the popularity of VPNs with torrent users, permissible activity on specific VPNs can vary. Some companies disallow torrents completely, some are totally fine with them, while others won’t stop torrents but officially disallow them. We aren’t here to advise pirates, but anyone looking to use a VPN should understand what is and is not okay to do on their provider’s network.
Finally, does the VPN provider offer their own application that you can download and install? Unless you’re a power user who wants to mess with OpenVPN, a customized VPN program is really the way to go. It’s simple to use and doesn’t require any great technical knowledge or the need to adjust any significant settings.
Using a VPN
You’ve done your due diligence, checked out your VPN’s logging policies, and found a service with a great price and a customized application. Now, for the easy part: connecting to the VPN.
Here’s a look at a few examples of VPN desktop applications.
TunnelBear (reviewed here) has a very simple interface. All you need to do is select the country you want to be virtually present in, click the slider to “on,” and wait for a connection-confirmation message.
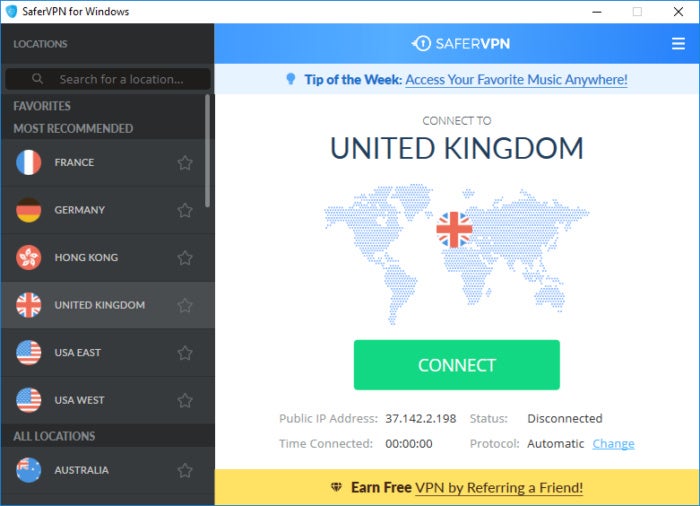
SaferVPN (reviewed here) works similarly. From the left-hand side you select the country you’d like to use—the more common choices such as the U.S., Germany, and the U.K. are at the top. Once that’s done, hit the big Connect button and wait once again for the confirmation message.
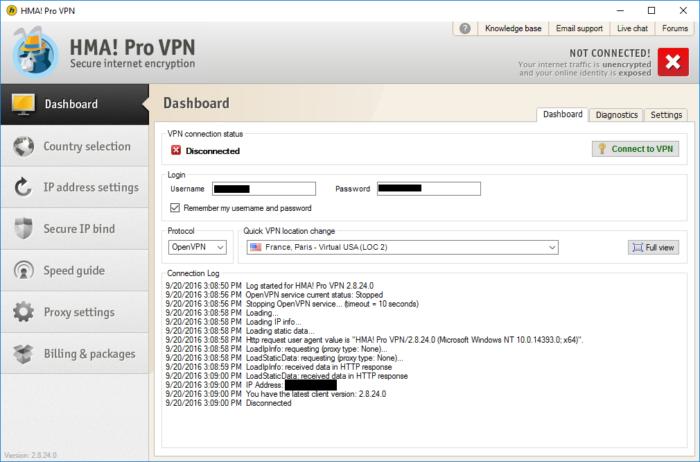
HMA Pro is slightly more complicated, but it’s far from difficult to understand. If you want to select your desired virtual location click the Location mode tab, click on the location name, and then choose your preferred location from the list. Once that’s done, click the slider button that says Disconnected. Once it flips to Connected, you’re ready to roll.
There are numerous VPN services out there, and they all have different interfaces; but they are all similar enough that if you can successfully use one, you’ll be able to use the others.
That’s all there is to using a VPN. The hard part is figuring out which service to use. Once that’s done, connecting to a VPN for added privacy or to stream your favorite TV shows while abroad is just a click away.

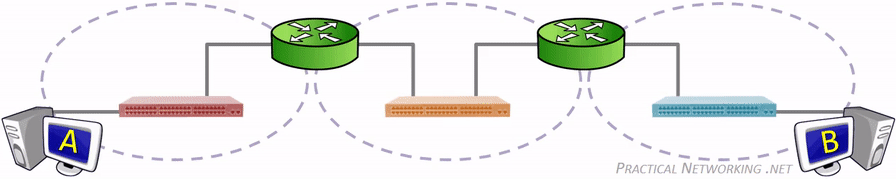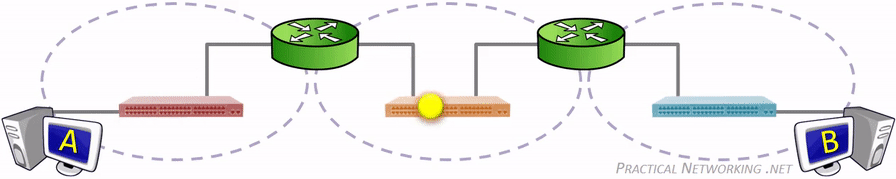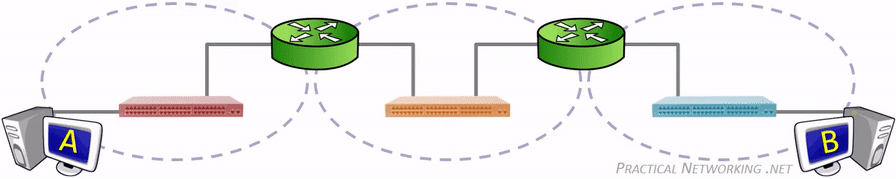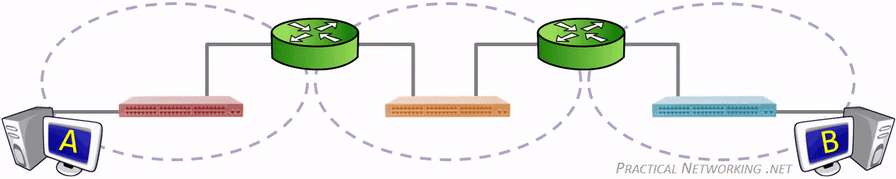
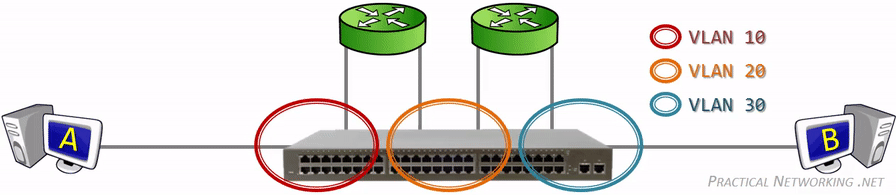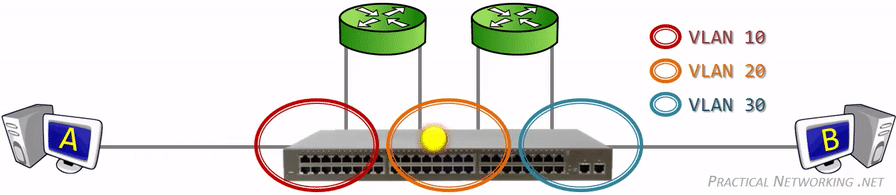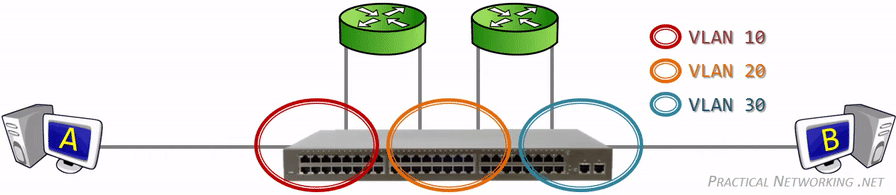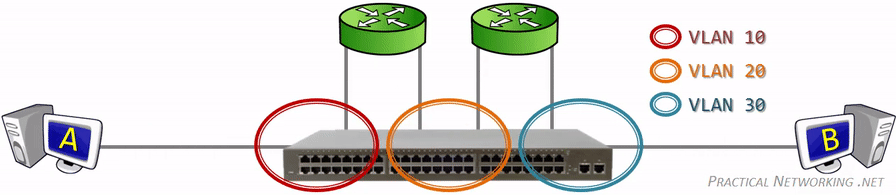
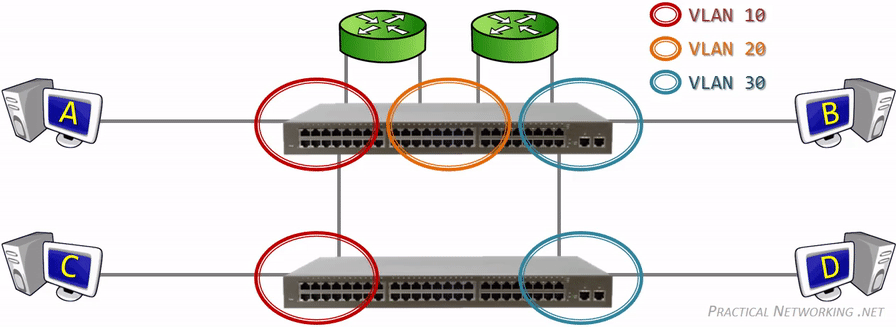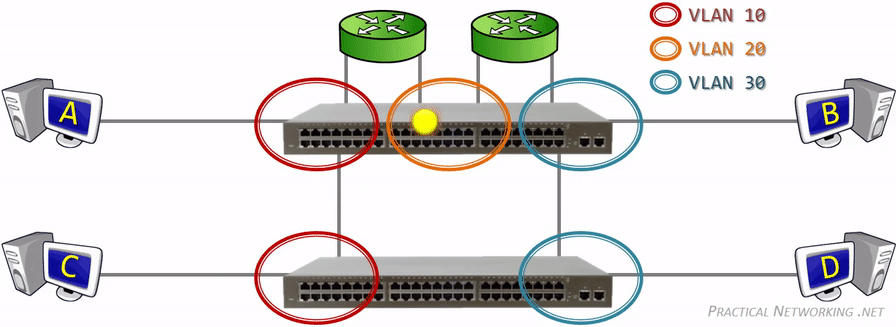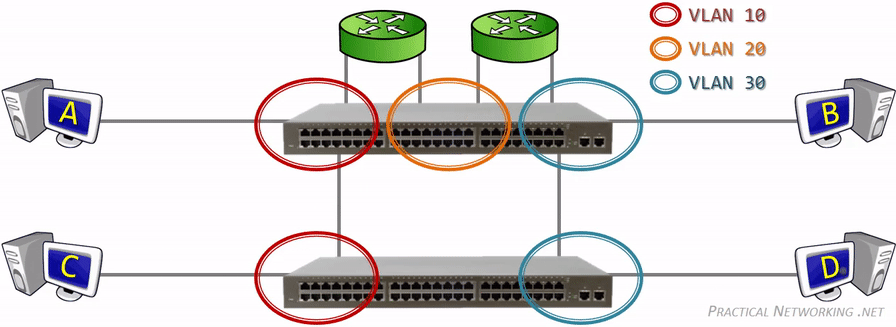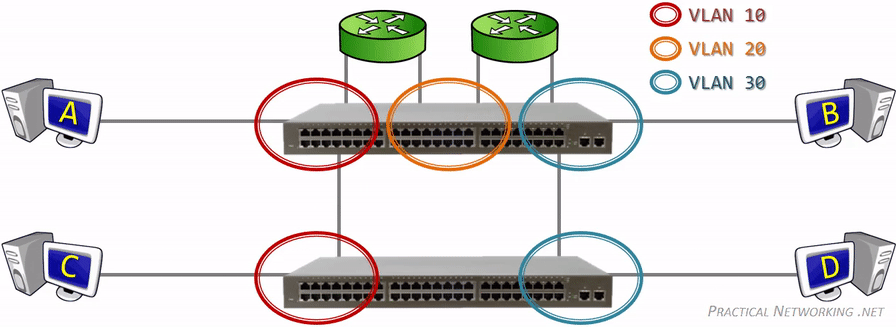
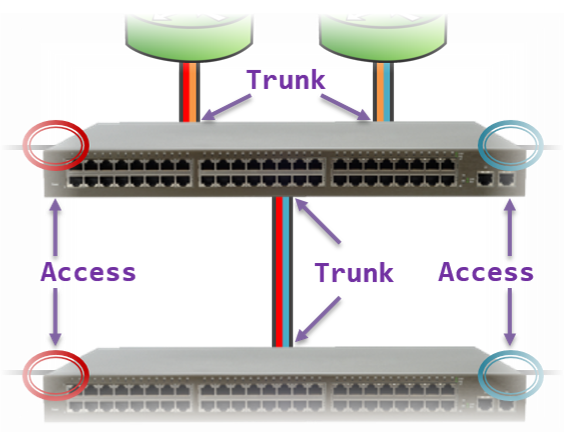
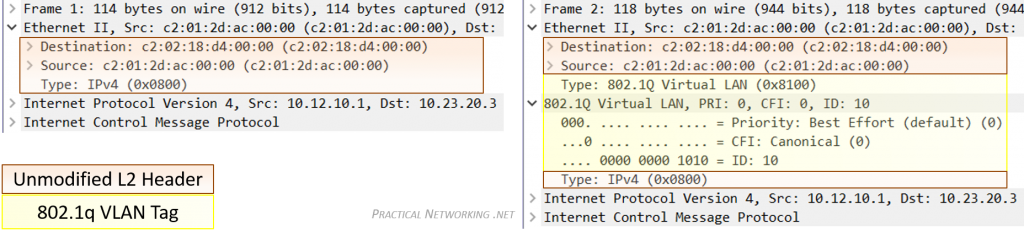
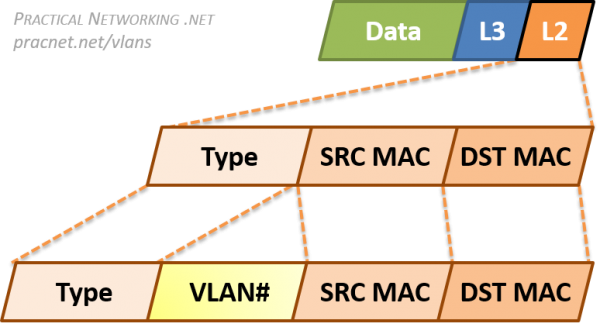 Since VLANs are a Layer 2 technology, the VLAN Tag is inserted within the Layer 2 header. The standard Layer 2 header in modern networks is the
Since VLANs are a Layer 2 technology, the VLAN Tag is inserted within the Layer 2 header. The standard Layer 2 header in modern networks is the